Table of Contents
What is ModSecurity?
ModSecurity is like a vigilant guardian for websites and web applications. It’s an open-source web application firewall (WAF) that acts as an external security layer, constantly monitoring and filtering traffic into your web server.
Much like a bouncer at a club, ModSecurity decides who gets in and who doesn’t based on a predefined set of rules. So it can detect and prevent attacks before they reach your server to harm web programs and steal your data.
Do you know? Initially, ModSecurity code was designed for Apache HTTP web servers in 2002, but later on, it was modified for many other web servers, such as MS IIS and Nginx.
To detect upcoming threats, The mod security module is installed within the website server or as a proxy server in front of a website application. This allows the ModSecurity module to scan incoming and outgoing Hypertext transfer protocol (HTTP) communication to the endpoint. This Modsecurity core rule set (CRS) will decide how to handle that communication request. It has access to pass, drop, redirect, or return any HTTP request.
What are ModSecurity Rules?
Think of ModSecurity rules as the instructions given to our virtual security guard. These rules define what is considered a threat or an attack. When traffic enters the web server, ModSecurity compares it against these rules.
If the traffic (HTTP communication) matches any rule, it takes the necessary action to either allow or block it. As of 2023, the ModSecurity Rule Set is one of the most used code structures by web security software to detect and prevent cyber-attacks.
ModSecurity rules fall into different categories, each serving a unique purpose:
- Core Rules: These are the fundamental rules provided by the Open Web Application Security Project (OWASP). They cover a wide range of common web application vulnerabilities, offering a good baseline for protection.
- Custom Rules: These rules are tailored to specific applications or organizations. They address unique security concerns based on the specific setup and needs.
- Inbound Rules: These rules analyze incoming traffic to the web server, looking for potential threats and suspicious activities.
- Outbound Rules: Outbound rules of modsecurity focus on traffic leaving the web server. They aim to prevent data leakage or unauthorized communication.
Most common errors
The most common error triggered by a mod_security rule on our shared servers is 403 Forbidden one:
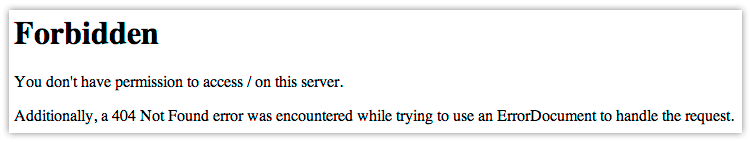
It simply states that you do not have permission to access / on the server. Depending on the exact link where you get the error, the path may vary.
ModSecurity works in the background, and every page request is being checked against various rules to filter out those requests which seem malicious. These can be the ones that have been run to exploit vulnerabilities in your website software with the only goal to hack the site.
Sometimes, due to poor website coding, mod_security may incorrectly determine that a certain request is malicious, while it is actually legitimate. When it happens, you still get a 403 error.
NOTE: Besides the 403 Forbidden error, you may also receive 404 Not Found or 500 Internal Server Error errors.
Some simple steps to detect mod_security block are as follows:
- You get one of the specified errors on your website frontend or backend when performing certain actions/requests: 403 Forbidden, 500 Internal Server Error, 404 Not Found.
- The way to reproduce the error is usually the same all the time (as far as mod_security blocks a certain activity only).
- The other functionality on your website frontend/backend remains normal.
NOTE: If mod_security rules are triggered too often on your website(-s), the corresponding IP address (the one those requests are sent from) will be blocked by the server firewall. This will result in your cPanel account being completely unavailable from this IP.
ModSecurity rule(-s) may be whitelisted by our support team only. It is also possible to disable mod_security for a specific domain name and the account in whole, but you should understand the risks once the specified module is off.

